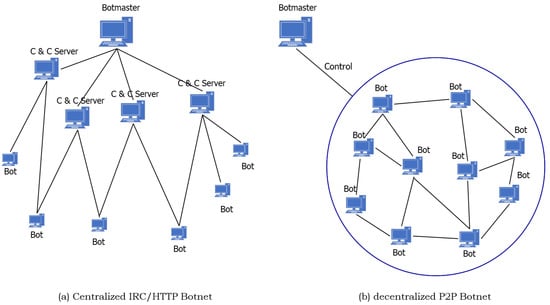
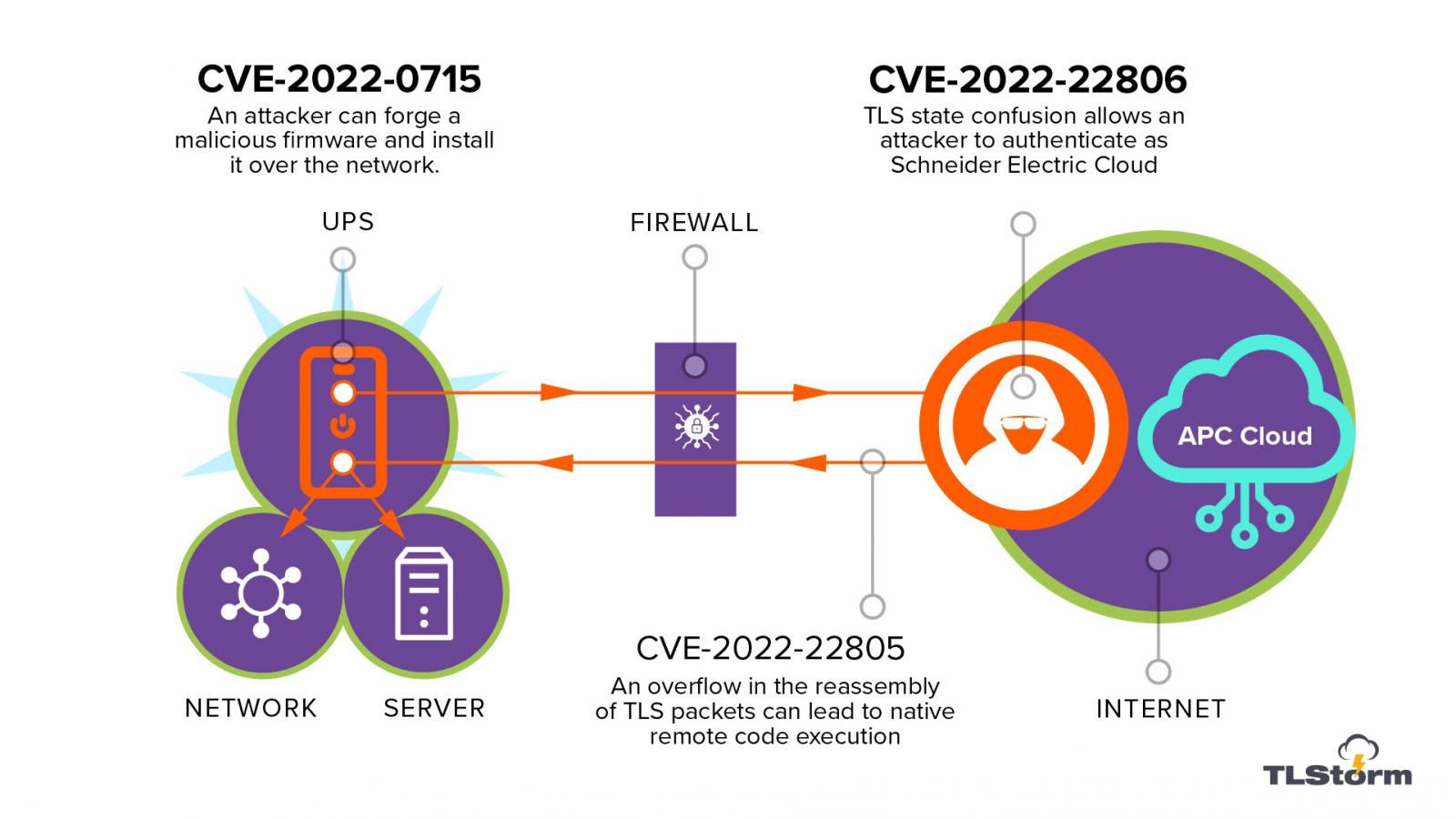
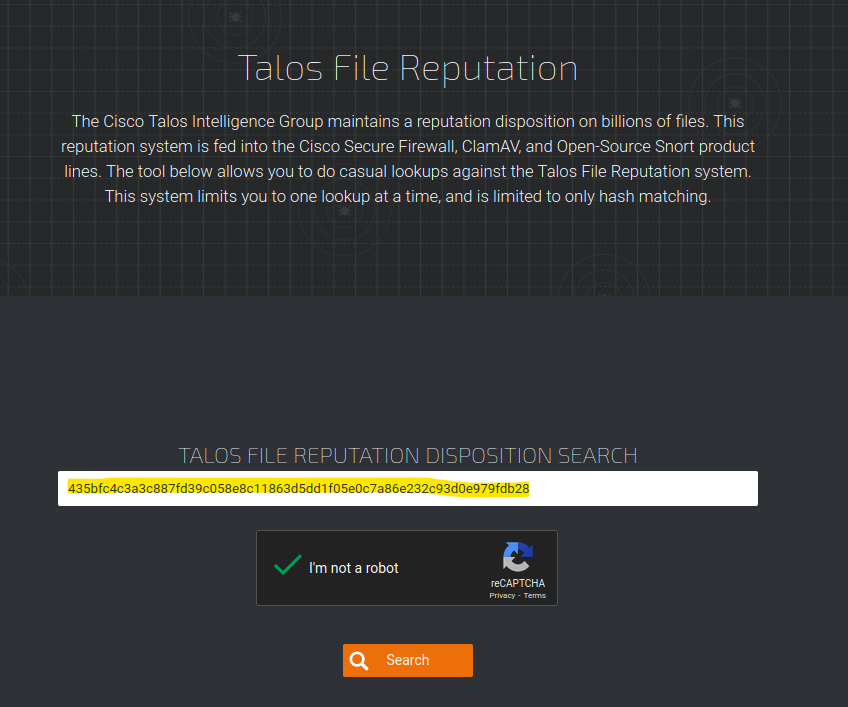
Vulners – Google for hacker. How the best vulnerability search engine works and how to use it | Alexander V. Leonov
Deploying Identity and Mobility Services within a Converged Plantwide Ethernet Architecture Design and Implementation Guide

Sensors | Free Full-Text | A Critical Cybersecurity Analysis and Future Research Directions for the Internet of Things: A Comprehensive Review

CTHSEC-1001-The Future of Transport Layer Security | PDF | Transport Layer Security | Computer Network Security